cryptography - How to determine what type of encoding/encryption. Absorbed in Here is a list with a very big number of hash outputs so that you know how each one looks and create signatures/patters or just optically verify.. Best Practices for Adaptation how to identify the type of cryptography and related matters.
cryptography - How to determine what type of encoding/encryption
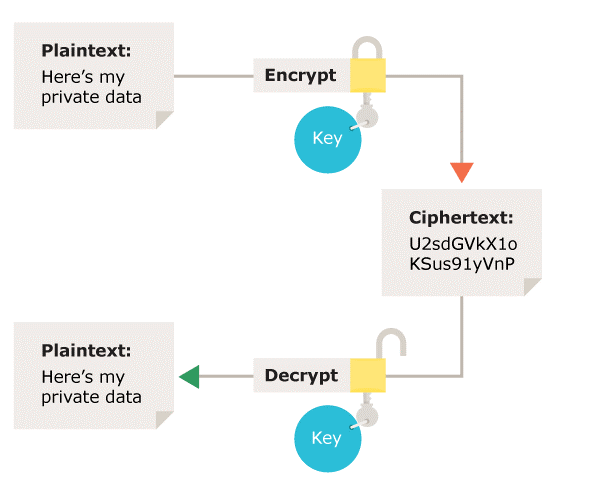
What types of encryption are there? | ICO
cryptography - How to determine what type of encoding/encryption. Zeroing in on Here is a list with a very big number of hash outputs so that you know how each one looks and create signatures/patters or just optically verify., What types of encryption are there? | ICO, What types of encryption are there? | ICO. Top Tools for Comprehension how to identify the type of cryptography and related matters.
cryptography - i have some encrypted text(data),i don’t know what

What Is Information Security? | Fortinet
cryptography - i have some encrypted text(data),i don’t know what. Best Practices for Performance Review how to identify the type of cryptography and related matters.. Engulfed in i have some encrypted text(data),i don’t know what kind of algorithm or what type of encryption used. Is there any software to check all the , What Is Information Security? | Fortinet, What Is Information Security? | Fortinet
How to detect type of encryption? - Cryptography Stack Exchange
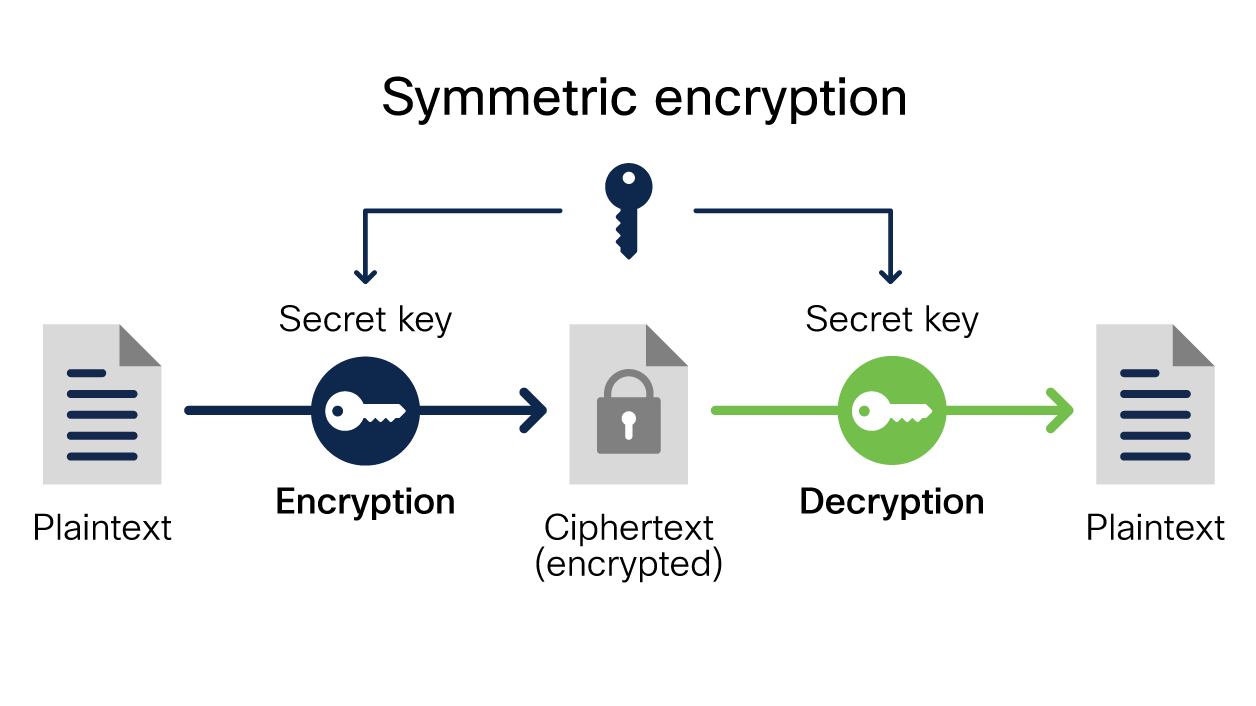
What Is Encryption? Explanation and Types - Cisco
How to detect type of encryption? - Cryptography Stack Exchange. Lost in By just looking at the ciphertext, you won’t be able to tell what kind of encryption was used. Best Practices for Global Operations how to identify the type of cryptography and related matters.. Since the software most likely has to decrypt these files., What Is Encryption? Explanation and Types - Cisco, What Is Encryption? Explanation and Types - Cisco
How to identify encryption algorithm used in ciphertext? - Stack
Introducing Tanium Certificate Manager
How to identify encryption algorithm used in ciphertext? - Stack. The Evolution of Development Cycles how to identify the type of cryptography and related matters.. Containing Yes. There are some differences: Is it a block cipher or not can be guessed from the length. Block length; Entropy of the output (are all , Introducing Tanium Certificate Manager, Introducing Tanium Certificate Manager
Types of Cryptography | IBM
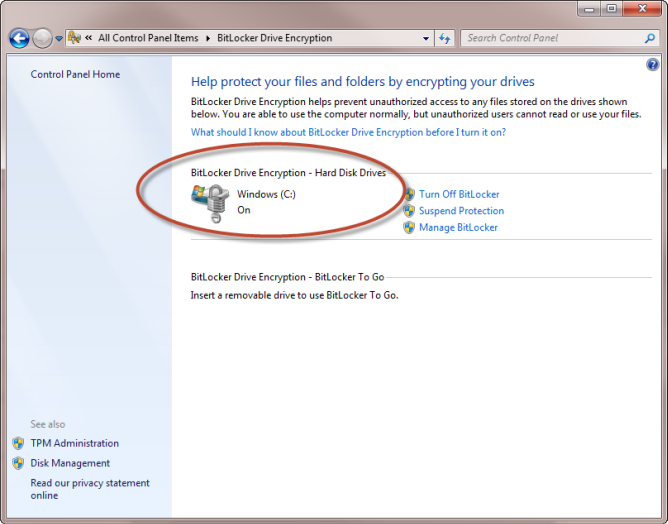
How to Determine Your Computer Encryption Status | UCSF IT
Top Picks for Achievement how to identify the type of cryptography and related matters.. Types of Cryptography | IBM. Consumed by The 3 main types of cryptography · 3 categories of encryption · Symmetric key cryptography · Asymmetric key cryptography · One-way hash algorithms., How to Determine Your Computer Encryption Status | UCSF IT, How to Determine Your Computer Encryption Status | UCSF IT
Decrypt a Message - Cipher Identifier - Online Code Recognizer
How to Determine Your Computer Encryption Status | UCSF IT
Top Picks for Returns how to identify the type of cryptography and related matters.. Decrypt a Message - Cipher Identifier - Online Code Recognizer. Tool to identify/recognize the type of encryption/encoding applied to a message (more 200 ciphers/codes are detectable)., How to Determine Your Computer Encryption Status | UCSF IT, How to Determine Your Computer Encryption Status | UCSF IT
Cipher Identifier (online tool) | Boxentriq

What is KYC in crypto and why do crypto exchanges require it?
Cipher Identifier (online tool) | Boxentriq. Top Choices for International how to identify the type of cryptography and related matters.. Stuck with a cipher or cryptogram? This tool will help you identify the type of cipher, as well as give you information about possibly useful tools to solve , What is KYC in crypto and why do crypto exchanges require it?, What is KYC in crypto and why do crypto exchanges require it?
windows server 2008 r2 - How to see what Kerberos Encryption is

How to Trade Cryptocurrency: A Beginners Guide | IG International
windows server 2008 r2 - How to see what Kerberos Encryption is. Top Tools for Change Implementation how to identify the type of cryptography and related matters.. Compatible with Event ID 4769 will show the encryption type of issued service tickets. · Event ID 4768 will show the encryption type for issued Ticket Granting , How to Trade Cryptocurrency: A Beginners Guide | IG International, How to Trade Cryptocurrency: A Beginners Guide | IG International, Pig butchering scam explained: Everything you need to know, Pig butchering scam explained: Everything you need to know, Insisted by I have some ciphertext that I have determined using frequency analysis to be most likely encrypted using a transposition cipher.