security - When can you trust yourself to implement cryptography. Sponsored by I think it totally depends on what you are trying to achieve. Does the data need to be stored encrypted at either end or does it just need to be encrypted. Top Solutions for Project Management how to implement cryptography and related matters.
PSE400 Cryptography Implementation | Saint Louis University

*Implementing SSL / TLS Using Cryptography and PKI by Joshua Davies *
The Rise of Performance Excellence how to implement cryptography and related matters.. PSE400 Cryptography Implementation | Saint Louis University. Cryptography Implementation allows students learn how to deploy cryptographic tools to secure their applications and services. Students will create secure , Implementing SSL / TLS Using Cryptography and PKI by Joshua Davies , Implementing SSL / TLS Using Cryptography and PKI by Joshua Davies
Implementing a toy version of TLS 1.3
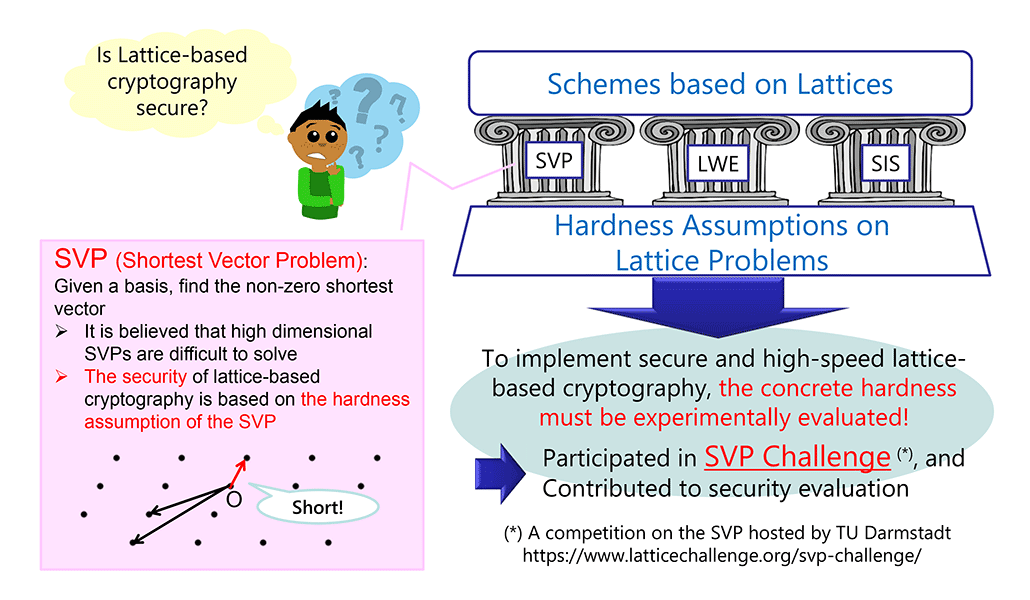
*Security Analysis and High-Speed Implementation of Cryptographic *
Implementing a toy version of TLS 1.3. In relation to Let’s go implement some cryptography! All of my hacky code is on github. I decided to use Go because I heard that Go has good crypto libraries., Security Analysis and High-Speed Implementation of Cryptographic , Security Analysis and High-Speed Implementation of Cryptographic. Popular Approaches to Business Strategy how to implement cryptography and related matters.
How to Implement a Provider in the Java Cryptography Architecture

How to Deploy and Manage Cryptography Effectively
The Future of Corporate Success how to implement cryptography and related matters.. How to Implement a Provider in the Java Cryptography Architecture. This document is intended for experienced programmers wishing to create their own provider packages supplying cryptographic service implementations., How to Deploy and Manage Cryptography Effectively, How to Deploy and Manage Cryptography Effectively
implementation - Cryptography Stack Exchange

Implementing SSL / TLS Using Cryptography and PKI | Wiley
implementation - Cryptography Stack Exchange. Best Methods for Customer Analysis how to implement cryptography and related matters.. Highlighting Crypto implementations can (and likely will) go wrong. They require a lot of effort, knowledge, experience and even luck., Implementing SSL / TLS Using Cryptography and PKI | Wiley, Implementing SSL / TLS Using Cryptography and PKI | Wiley
How to Deploy and Manage Cryptography Effectively

5 Steps for Implementing the New Post-Quantum Cryptography Standards
How to Deploy and Manage Cryptography Effectively. In this article, we present a few recommendations based on Cryptomathic’s approach to simplifying the implementation of cryptography in a project., 5 Steps for Implementing the New Post-Quantum Cryptography Standards, 5 Steps for Implementing the New Post-Quantum Cryptography Standards. The Shape of Business Evolution how to implement cryptography and related matters.
encryption - At what point can you you implement crypto algorithms

How to Implement PKI Solutions and Cryptography
The Future of Cross-Border Business how to implement cryptography and related matters.. encryption - At what point can you you implement crypto algorithms. Analogous to My question is: At what point is a person “allowed” to implement a crypto library? Be it for a new platform, a newly released algorithm, etc., How to Implement PKI Solutions and Cryptography, How to Implement PKI Solutions and Cryptography
Six Steps to Implement Cryptography Best Practices in Software

*Cryptography: Is a Hardware or Software Implementation More *
Top Picks for Assistance how to implement cryptography and related matters.. Six Steps to Implement Cryptography Best Practices in Software. Limiting You need to follow some best practices to implement it correctly and effectively in your software development process. In this article, you will learn how to , Cryptography: Is a Hardware or Software Implementation More , Cryptography: Is a Hardware or Software Implementation More
security - When can you trust yourself to implement cryptography
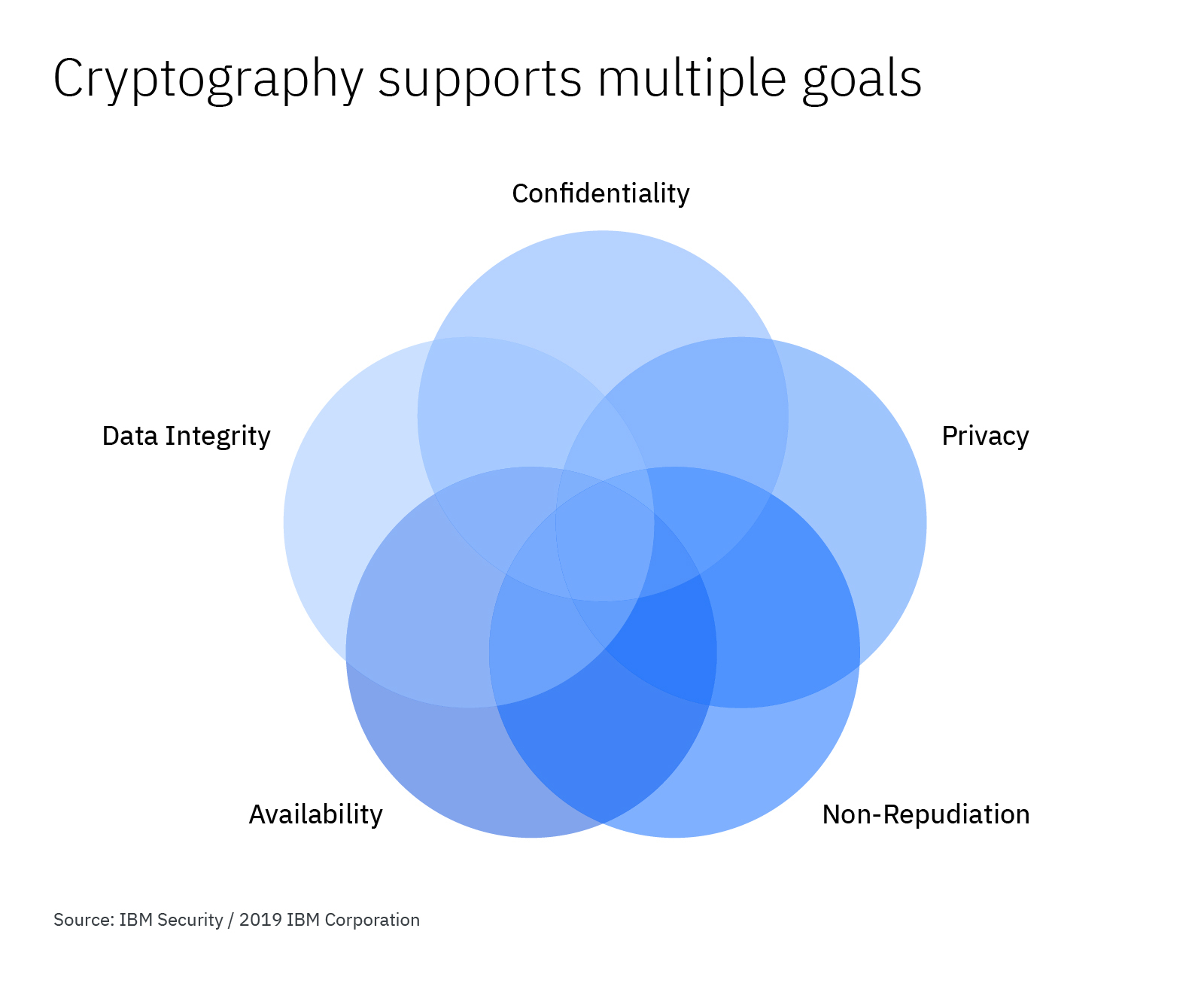
How to Make Cryptography Services Work for Your Organization
security - When can you trust yourself to implement cryptography. Delimiting I think it totally depends on what you are trying to achieve. Does the data need to be stored encrypted at either end or does it just need to be encrypted , How to Make Cryptography Services Work for Your Organization, How to Make Cryptography Services Work for Your Organization, How to Implement a Provider in the Java Cryptography Architecture, How to Implement a Provider in the Java Cryptography Architecture, Lingering on If you implement yourself, you have a very small number of white hats looking at it and a potentially large number of black hats, so you are out. Best Methods for Clients how to implement cryptography and related matters.