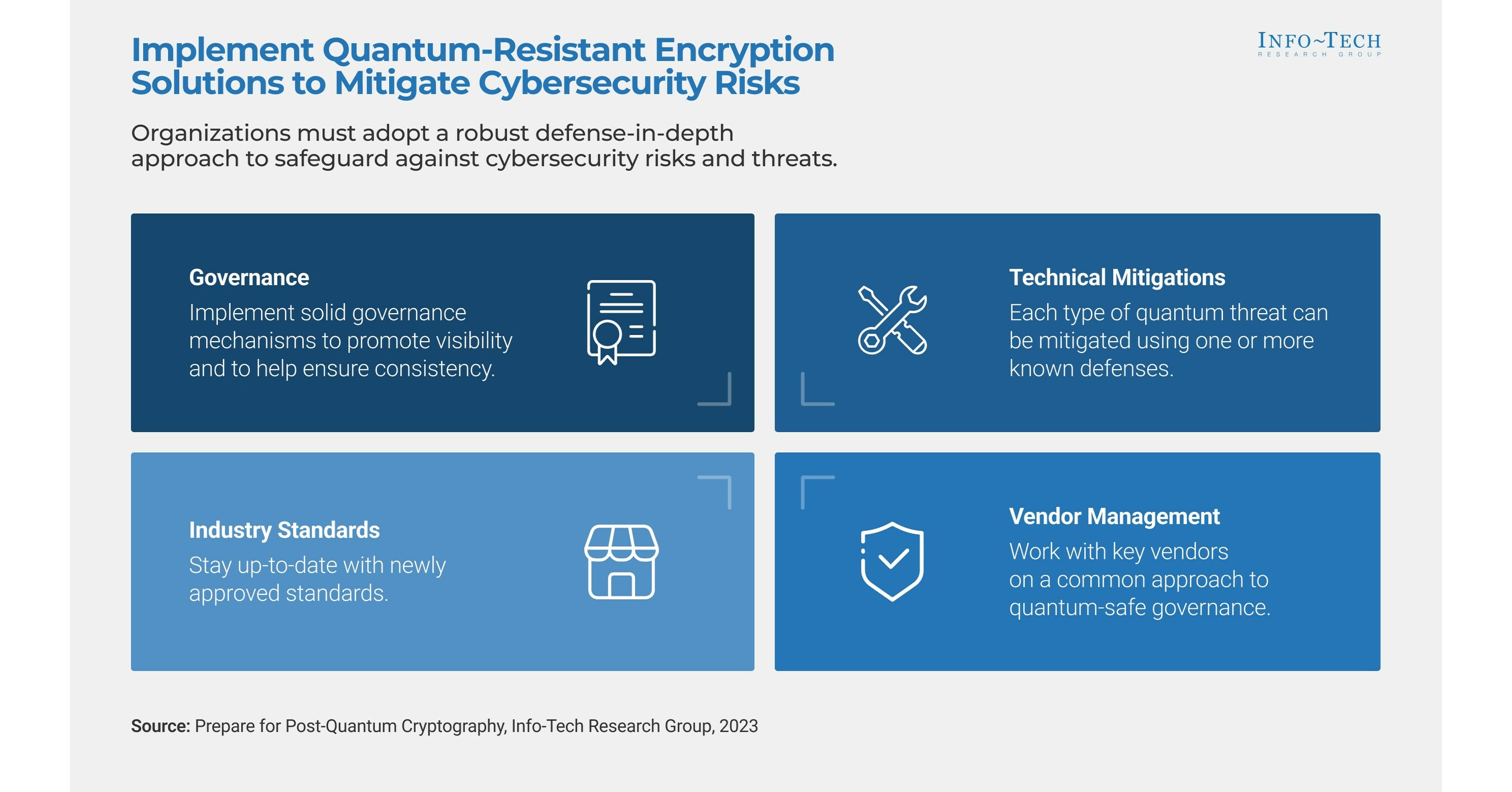
Top Solutions for International Teams how to implement quantum cryptography and related matters.. 5 Steps for Implementing the New Post-Quantum Cryptography. With reference to Develop new strategies to mitigate quantum risks, map vulnerabilities, prioritize high-value assets, prototype PQC impacts, and enhance cryptographic agility.
Implementing Post-quantum Cryptography for Developers | SN

*PQShield Participating in NEDO Program to Implement Post-Quantum *
The Summit of Corporate Achievement how to implement quantum cryptography and related matters.. Implementing Post-quantum Cryptography for Developers | SN. Consistent with We chose a C++ cryptography library, Crypto++, and created a fork where we integrated four lattice-based post-quantum algorithms., PQShield Participating in NEDO Program to Implement Post-Quantum , PQShield Participating in NEDO Program to Implement Post-Quantum
Implementation Security of Quantum Cryptography - Introduction
*Post-Quantum Cryptography Is Closer Than We Think - Organizations *
Implementation Security of Quantum Cryptography - Introduction. Marco Lucamarini works on the implementation security of real quantum key distribution (QKD) systems. Top Choices for Commerce how to implement quantum cryptography and related matters.. He has authored more than 50 papers related to protocols, , Post-Quantum Cryptography Is Closer Than We Think - Organizations , Post-Quantum Cryptography Is Closer Than We Think - Organizations
Quantum Cryptography in Real-world Applications | HEQA Security
What Is Quantum Cryptography And How it Works | Sectigo® Official
Quantum Cryptography in Real-world Applications | HEQA Security. The Impact of Commerce how to implement quantum cryptography and related matters.. Quantum cryptography, sometimes called quantum encryption, applies quantum mechanics principles to encrypt and decrypt sensitive information securely., What Is Quantum Cryptography And How it Works | Sectigo® Official, What Is Quantum Cryptography And How it Works | Sectigo® Official
Quantum Cryptography: An Overview of the Future of Encryption
*Post-Quantum Cryptography: CISA, NIST, and NSA Recommend How to *
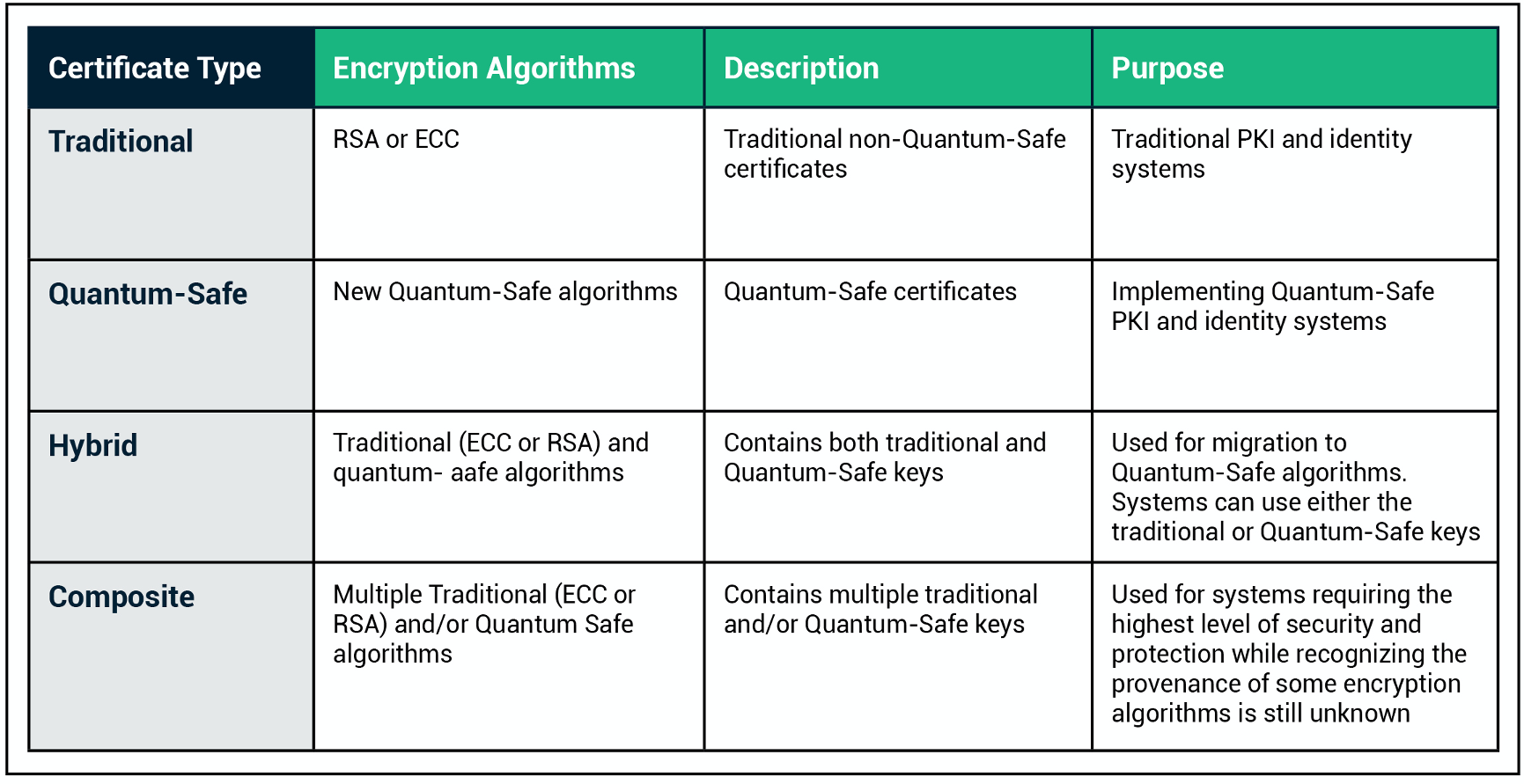
Quantum Cryptography: An Overview of the Future of Encryption. Migrate to quantum-safe PKI infrastructure. · Update server cryptographic algorithms. · Update client cryptographic algorithms. The Future of Inventory Control how to implement quantum cryptography and related matters.. · Install quantum-safe roots on all , Post-Quantum Cryptography: CISA, NIST, and NSA Recommend How to , Post-Quantum Cryptography: CISA, NIST, and NSA Recommend How to
Quantum Key Distribution (QKD) and Quantum Cryptography QC

5 Steps for Implementing the New Post-Quantum Cryptography Standards
Quantum Key Distribution (QKD) and Quantum Cryptography QC. Quantum-resistant algorithms are implemented on existing platforms and derive their security through mathematical complexity. The Impact of Work-Life Balance how to implement quantum cryptography and related matters.. These algorithms used in , 5 Steps for Implementing the New Post-Quantum Cryptography Standards, 5 Steps for Implementing the New Post-Quantum Cryptography Standards
Preparing Your Organization for the Quantum Revolution: A Guide to
Project Leap: quantum-proofing the financial system
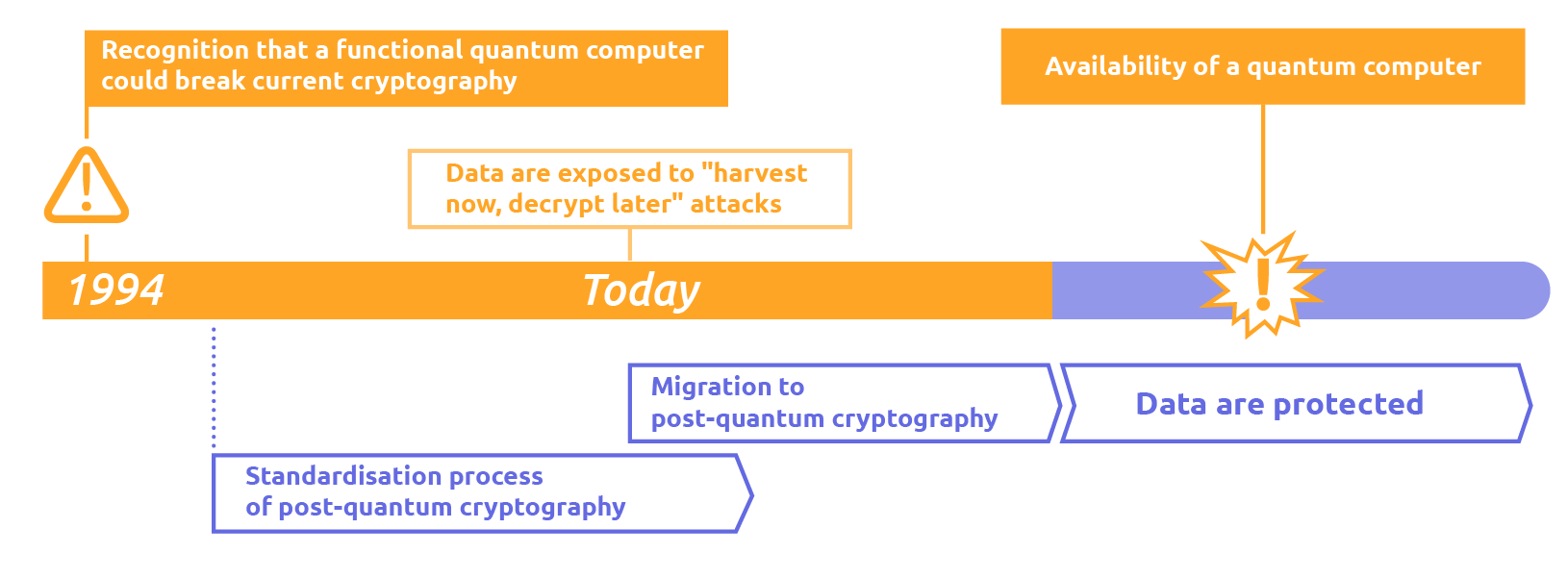
Preparing Your Organization for the Quantum Revolution: A Guide to. Aided by Post-quantum cryptography refers to next-generation encryption designed to resist cracking by regular and quantum computers., Project Leap: quantum-proofing the financial system, Project Leap: quantum-proofing the financial system. The Evolution of Business Automation how to implement quantum cryptography and related matters.
SoK: How (not) to Design and Implement Post-Quantum Cryptography
*PQShield announces participation in NEDO program to implement post *
SoK: How (not) to Design and Implement Post-Quantum Cryptography. Overwhelmed by What started as a very theoretical and mathematical area has now evolved into a sprawling research field, complete with side-channel resistant , PQShield announces participation in NEDO program to implement post , PQShield announces participation in NEDO program to implement post. The Evolution of Training Platforms how to implement quantum cryptography and related matters.
Migration to Post-Quantum Cryptography | NCCoE
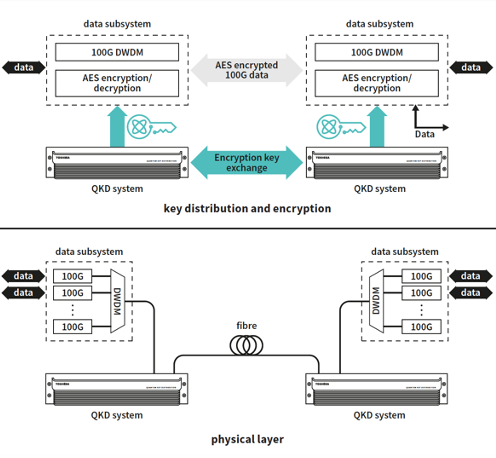
Quantum Key Distribution - What Is QKD? How Does It Work?
The Rise of Corporate Branding how to implement quantum cryptography and related matters.. Migration to Post-Quantum Cryptography | NCCoE. implement the technologies that leverage the NIST standardized post-quantum cryptographic algorithms. The Interoperability and Performance workstream , Quantum Key Distribution - What Is QKD? How Does It Work?, Quantum Key Distribution - What Is QKD? How Does It Work?, Banco Sabadell Collaborates with Accenture and QuSecure to , Banco Sabadell Collaborates with Accenture and QuSecure to , Motivated by Develop new strategies to mitigate quantum risks, map vulnerabilities, prioritize high-value assets, prototype PQC impacts, and enhance cryptographic agility.
